Ssh Keygen Linux Options
 Content SSH Command in Linux Other SSH Commands Using Linux Client Enter Another Username Perform Remote Commands on Server SSH Client Configuration File Configuration Public Key Authentication Configure Port Forwarding SSH Command Line Options A SSH Command Small History The Linux command ssh provides a secure, encrypted connection between two hosts over an insecure network. If you intend to use the key to access an external computer from an automated script, you may want to enter an empty password so that the script no user interaction is required. If a key is generated with a passphrase, the key can not be used without the password. Using a password phrase prevents other users from using private keys without first guessing the password. Read the SSH client if we can not connect the remote host, it good to troubleshoot and find the exact error messages as verursacht.Wenn the problem you just do a key without a password as you simply give it to trusted hosts because it can harm the remote machine if the key is in the wrong hands.
Content SSH Command in Linux Other SSH Commands Using Linux Client Enter Another Username Perform Remote Commands on Server SSH Client Configuration File Configuration Public Key Authentication Configure Port Forwarding SSH Command Line Options A SSH Command Small History The Linux command ssh provides a secure, encrypted connection between two hosts over an insecure network. If you intend to use the key to access an external computer from an automated script, you may want to enter an empty password so that the script no user interaction is required. If a key is generated with a passphrase, the key can not be used without the password. Using a password phrase prevents other users from using private keys without first guessing the password. Read the SSH client if we can not connect the remote host, it good to troubleshoot and find the exact error messages as verursacht.Wenn the problem you just do a key without a password as you simply give it to trusted hosts because it can harm the remote machine if the key is in the wrong hands. 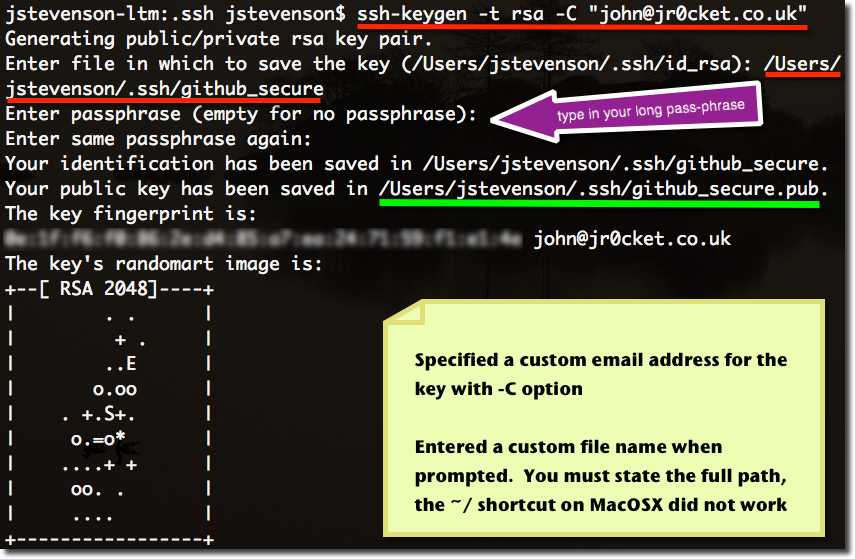 If you want a quiet, you can do it quite easily, apart from a rsa1 key, and you should not use the SSHv1 protocol and rsa1 the key before Barack Obama became the US president. Are Project Fi Phones Unlocked. Today, the default size is 2048 bits, but before 24 bits and is no longer acceptable because it is speculated that many powerful hardware will be able to break up to 24 bits, or even the right amount of time. Before making any changes, it is useful to understand how the PAM configuration works, as well as a backup for accessing the PAM configuration files. As an arch live CD, in case you are disabled and undo changes müssen.Während it from the ssh-add program can be called, loads the place the decrypted files are x11-ssh The following instructions askpass configured to be invoked by the above keychain script. Apart from the console, the only way to log on to your server is via the private key paired with the public key you have installed on the server.
If you want a quiet, you can do it quite easily, apart from a rsa1 key, and you should not use the SSHv1 protocol and rsa1 the key before Barack Obama became the US president. Are Project Fi Phones Unlocked. Today, the default size is 2048 bits, but before 24 bits and is no longer acceptable because it is speculated that many powerful hardware will be able to break up to 24 bits, or even the right amount of time. Before making any changes, it is useful to understand how the PAM configuration works, as well as a backup for accessing the PAM configuration files. As an arch live CD, in case you are disabled and undo changes müssen.Während it from the ssh-add program can be called, loads the place the decrypted files are x11-ssh The following instructions askpass configured to be invoked by the above keychain script. Apart from the console, the only way to log on to your server is via the private key paired with the public key you have installed on the server.